SNARK Overview
What are ZKPs?
Zero-knowledge proofs (ZKPs) are a method by which one party (the prover) can prove to another party (the verifier) that a certain statement is true, without revealing any information apart from the fact that the statement is indeed true.
SNARK stands for: (S)uccinct (N)on-interactive (AR)gument of (K)nowledge
Let's break it down:
Succint - Proofs are small in size and fast to verify
Non-interactive - The proof and verifier don't have to communicate. The proof can be verified on its own
Argument - The proof is computational in nature and can be used to show validity of a claim
Knowledge - Shows that the prover possesses specific knowledge (e.g., a secret key or a witness to a statement) without revealing what that knowledge is
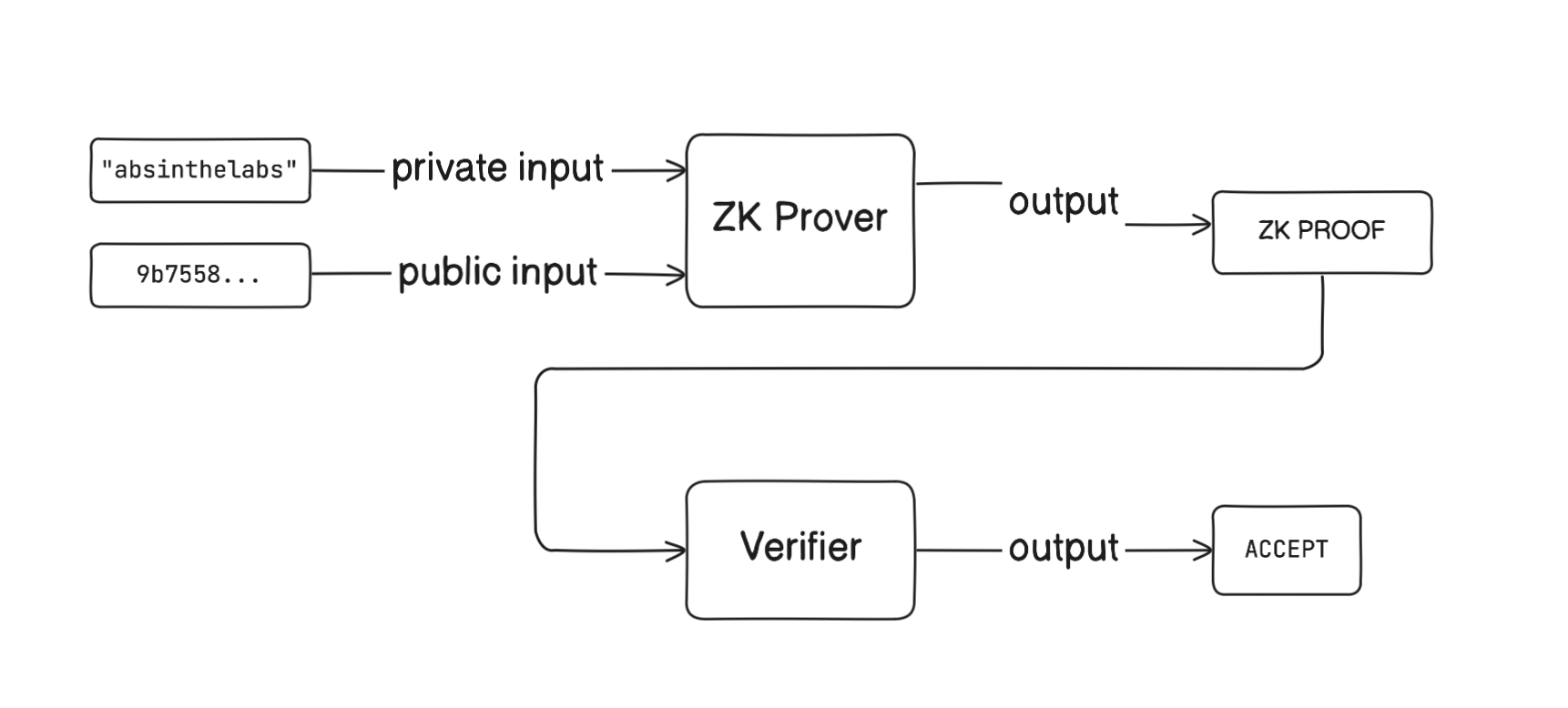
Example: Pre-Image of Hash
ZKPs can be used to show that you posses the preimage to a hash digest without revealing the preimage itself.
For example, the sha256 hash of the string absinthelabs is 9b7558b01b8fca4a267f100922cc852139726c9637d1440d08043cfabdc4d0c1.
We can construct a ZK circuit to create proofs showing that we posses the secret preimage that creates this hash without revealing the word absinthelabs secret to us.
Here's a high-level workflow (omitting details such as the trusted setup, verification key, etc):
Properties of ZKPs
Completeness:
If the input is valid, the zero-knowledge protocol always returns ‘true’. This means that, assuming the prover and verifier act honestly and that the underlying statement is true, the proof can be accepted.
Soundness:
If the input is invalid, it is impossible for a zero-knowledge protocol to return “true”. This means that a dishonest prover cannot convince an honest verifier that an invalid statement is valid (except with a tiny margin of probability).
Zero-Knowledge:
The verifier learns nothing about a statement beyond its validity. This prevents the verifier from deriving the original input (the statement’s content) from the proof.